Thursday, November 29, 2018
Four times more Sunni Islamist militants today than on 9/11, study finds

There are four times as many Sunni Islamist militants today in the world than on September 11, 2001, despite an almost 20 year-long war campaign by the United States and its allies, according to a new report. Washington launched the ‘global war on terrorism’ in the aftermath of the 9/11 attacks that were perpetrated by al-Qaeda. In the ensuing years, American and other Western troops have engaged militarily in over a dozen countries, including Afghanistan, Iraq, Pakistan, Syria, Libya, Yemen, Somalia, Sudan, and the Philippines. But a new study by the bipartisan Center for Strategic and International Studies (CSIS) suggests that the West’s efforts to combat Sunni militancy are failing —and may even be making the problem worse. The report by the Washington-based think-tank states that the number of active Sunni Islamist militants today is as much as “270 percent greater than in 2001, when the 9/11 attacks occurred”.
Entitled “The Evolution of the Salafi-Jihadist Threat”, the 71-page report is one of the most extensive ever undertaken on this topic, drawing on information from data sets that date back nearly 40 years. It warns that, despite the rapid loss of territory suffered by the Islamic State in Iraq and Syria, armed Sunni militancy is “far from defeated”. The number of Salafi-jihadists —active proponents of armed fight against perceived enemies of Islam— has slightly declined in comparison to 2016, but it remains at near-peak levels over a 38-year period, says the CSIS report. It estimates that there are today as many as 230,000 Salafi-jihadists in almost 70 countries. Most of them are based in Syria (as many as 70,500), Afghanistan (as many as 64,000), Pakistan (up to 40,000), and Iraq (up to 15,000). Nearly 30,000 more are in Africa, primarily in Somalia, Nigeria and the Sahel region.
These fighters, and the groups they fight under, are far more resilient than Western antiterrorist strategists tend to assume, claims the report. They are also inadvertently aided by successive policy failures by the US and its closest Western allies. The latter focus primarily on the military aspects of counterterrorism campaigns, while ignoring the importance of improving local governance in territories where Sunni Islamism is rife, argues the report. Therefore, as the US and its allies continue to engage “in a seemingly endless [military] confrontation with a metastasizing set of militant groups”, they face seemingly endless waves of militants, who are becoming increasingly capable of resisting Western conventional military force. The report is available online in .pdf form, here.
► Author: Joseph Fitsanakis
Huawei: Why has UK not blocked Chinese firm's 5G kit?

New Zealand government's move to prevent Huawei supplying a local mobile network with 5G equipment has raised questions about why the UK appears less concerned about use of the Chinese company's technology.
A press release from Spark, the New Zealand company involved, said it had been deemed that the deployment posed "significant security risks" - a polite way of saying that Beijing might use the technology to spy on the country or disrupt its communications in a future dispute.
The US and Australia had already closed the door on Huawei's involvement in their next-generation mobile networks.
That means three members of the Five Eyes intelligence alliance have now acted against the Shenzhen-based company. And one other member, Canada, is carrying out a security review of its own.
So, there's a prospect that the UK could soon be the sole holdout, allowing Huawei to play a key role in delivering the data that everything from self-driving cars to smart city sensors will rely on.
"There are two factors at play here: 5G will be connected to everything as we go to the internet-of-things," said Ewan Lawson, from UK defence think tank Rusi.
"And concerns about foreign-sourced hardware were less intense than they are now."
For its part, Huawei has said: "[We are] aware of Spark's statement and we are looking into the situation.
"As a leading global supplier of telecoms equipment, we remain committed to developing trusted and secure solutions for our customers."
Is the UK just being complacent?
 Image copyrightGETTY IMAGES
Image copyrightGETTY IMAGES
The government argues not.
"This government and British telecoms operators work with Huawei at home and abroad to ensure the UK can continue to benefit from new technology while managing cyber-security risks," a Cabinet Office spokeswoman told BBC News.
That work includes a facility nicknamed the Cell, in Banbury, Oxfordshire, where staff employed by Huawei but answering to GCHQ hunt for security flaws in the company's products.
It has not uncovered evidence of hidden backdoors or other deliberate attempts of subterfuge. But its last report did identify shortcomings that led it to warn that it could offer only "limited assurance" that the company posed no threat.
The UK government is also thought to have fired a shot across the bows last month, when it wrote to telecoms companies warning that a review of their infrastructure could lead to "changes in the current rules" that should be taken into account during "procurement decisions".
Huawei was not mentioned by name, but the Financial Times - which revealed the letter's existence - said some industry executives interpreted it to mean a ban was still possible.
But others have their doubts, noting that other political factors are at play.
"The letter did go out but the issue remains that in the absence of any definitive evidence of a problem, an unspecific security risk has to be weighed against trade opportunities," said Mr Lawson.
"If Huawei was banned, we don't know the extent to which China might well refuse to do business with us in other fields - and the timing for that would not be great with so much attention on the potential economic impacts of Brexit."
How strong are Huawei's existing UK ties?
 Image copyrightGETTY IMAGES
Image copyrightGETTY IMAGES
Huawei opened its first office in the country in 2001 and soon had its equipment adopted by BT and Vodafone, which used it to support 2G, 3G and 4G mobile services as well as "superfast" fibre and other types of broadband connections to homes and businesses.
Its kit includes mobile phone radio antennas and the routers and switches found in kerbside cabinets.
Most of the country's mobile networks - Vodafone, EE and Three - are now working with Huawei to prepare their 5G offerings.
O2's parent Telefonica has also tested its new equipment elsewhere and signalled that it might use it in the UK.
In addition, Huawei says it has developed research and development partnerships with many of the country's leading academic institutions, including the Universities of Cambridge, Oxford, Cardiff and Imperial College.
Its UK board of directors includes Lord Browne, the former chief of BP, and Sir Andrew Cahn, a former high-ranking civil servant.
Does Huawei pose a real threat?
 Image copyrightGETTY IMAGES
Image copyrightGETTY IMAGES
The company is keen to portray itself as a private company owned by its employees with no ties to the Chinese government beyond those of a law-abiding taxpayer.
It can also lay claim to being one of the biggest spenders on research and development - it invested more than $13.2bn (£10.3bn) last year and has said the figure will be even higher for 2018.
But critics like to point out that its media-shy founder, Ren Zhengfei, was a former engineer in the country's army and joined the Communist Party in 1978.
Furthermore, they question how free any major Chinese business can be from Beijing's influence.
"It's accepted practice in China that relationships between Chinese companies and the state have to be extremely close," said Prof Anthony Glees, director of the Buckingham University Centre for Security and Intelligence Studies.
"Many other countries have said no [to Huawei over 5G].
"We've come to the matter late as we have already let them through the door."
Another leading cyber-security expert agreed that Huawei could be co-opted into incapacitating the equipment it had sold.
"The obvious concern with 5G is whether there is a material risk of the Chinese being in a position to run a big denial-of-service attack on Britain in the event of a time of international tension," said Ross Anderson, professor of security engineering at the University of Cambridge.
"There is obviously a risk. China plays hardball and we have been hoping in vain for years that it would get nice as it got richer but that hasn't happened."
For now, Beijing has been reticent to be seen to be too forceful in leaping to Huawei's defence.
The Chinese government did warn against "protectionism" when a deal to sell Huawei's phones in the US fell through and then "discriminatory practices" when Australia banned local networks using its 5G equipment.
But Chinese officials are already preoccupied with President Trump's threats of more trade tariffs and might see any effort to try to help Huawei as likely to backfire.
Even so, eyebrows have still been raised by a decision to exclude its founder from a list of 100 key contributors to China's economy over the past 40 years recently published in the Communist Party's People's Daily newspaper.
Whether that is because Mr Ren is viewed as being too close or not close enough to the government is unclear.
Norwegian spy service seeks right to break law during espionage operations

Norway’s supreme legislature body is considering a bill that would offer immunity from prosecution to intelligence officers and informants who are authorized by the country’s spy service to conduct espionage. The bill has been proposed on behalf of the Royal Norwegian Ministry of Defense, which supervises the operations of the Norwegian Intelligence Service (NIS), Norway’s primary intelligence agency. The NIS operates primarily abroad and is the only institution of the Norwegian state that can be authorized by the government to break laws in foreign countries. However, supporters of the new bill point out that NIS overseas operations can also break Norwegian law. That is something that the proposed bill addresses, they argue.
The proposed bill offers immunity from prosecution to NIS case officers and their assets —either informants or foreign spies— who may commit offenses under Norwegian law, as part of authorized espionage operations. In its consultation note that accompanies the proposed bill, the Norwegian Ministry of Defense admits that a number of NIS operations “already violate existing Norwegian laws”. That is inevitable, argues the Ministry, because officers and informants who engage in espionage operations will often “act contrary to the stipulations of criminal law […] as part of their assignments”. They may, in other words, “do certain things that would be illegal if they were done not on behalf of the intelligence service”, states the consultation note.
The document does not provide details of the types of offenses that are committed in pursuit of intelligence operations, arguing that “the offenses that the NIS commits, as well as its methods, must remain secret”. It does, however, suggest that intelligence officers may make use of “false or misleading identities, documents and information”. They may also “smuggle large amounts of cash from the country”, which they will use to pay foreign assets. Given that these assets receive Norwegian taxpayers’ funds, and that some of them end up settling in Norway, it is important that their proceeds not be considered taxable income under Norwegian law, according to the Defense Ministry. By reporting their revenue to the Norwegian Tax Administration, these assets would make their NIS connection known, and thus blow their cover, the document states.
The Defense Ministry notes that the new bill “will have little legal significance”, as NIS espionage operations are generally shielded from prosecution under Norway’s existing legal codes. It will, however, formalize the NIS’ legal scope and allow the agency to assure its case officers that they can perform their missions without fearing arrest or prosecution, so long as they act within the parameters of their authorized missions. The spy agency will also be able to recruit more “informants, sources and contractors”, says the document.
► Author: Joseph Fitsanakis
European Union agrees to establish joint intelligence training school

Twenty-five members of the European Union have agreed to establish a joint intelligence training academy, a move interpreted by some as a concrete effort to deepen inter-European security cooperation following Brexit. The announcement came just hours after leading EU heads of state spoke in favor of establishing a joint EU defense force. Calls for tighter cooperation between EU members in the areas of defense and security have been issued for decades. But the upcoming departure of Britain from the EU —popularly known as Brexit— has prompted Germany and France to propose deeper integration as a response to the rise of anti-EU sentiment across the continent.
The decision to establish a joint intelligence training school was approved on Monday by the ministers of defense and foreign affairs of 25 EU members. It was part of a wider agreement involving 16 other joint defense and security projects under the Permanent Structured Cooperation (PESCO) pact. The pact was first agreed on in September of 2017, and has since been functioning under the supervision of the European Defense Agency and the External Action Service —the diplomatic service of the EU. Nearly 20 projects of a military or security nature have since been signed under PESCO. Monday’s agreement virtually doubled the PESCO projects in existence. The new EU intelligence academy initiative will be led by Greece —an EU member since 1981— and will be headquartered in Cyprus, which joined the EU in 2004. When it becomes operational, the academy will provide “education and training in intelligence disciplines and other specific fields to EU member states’ intelligence personnel”, according to a joint PESCO communique issued on Monday.
The new intelligence school will work in cooperation with the individual intelligence agencies of the 25 co-signatory states, along with the North Atlantic Treaty Organization and with other regional security bodies, said PESCO. However, three EU states, namely Denmark, Malta and the United Kingdom, refused to support the project. Denmark and Malta are not participants in PESCO, while the United Kingdom is expected to leave the EU in March of next year. However, even before Brexit, London had vetoed the idea of closer EU intelligence cooperation, which it saw as a potential competitor to the so-called Five Eyes alliance, a postwar intelligence pact between the United States, the United Kingdom, Australia, New Zealand and Canada. Additionally, despite the overwhelming support for the intelligence academy by EU officials, it remains to be seen whether it will be realized. Observers told Politico on Monday that many other PESCO projects have “yet to get much beyond the drawing board” since their announcement last year.
► Author: Joseph Fitsanakis
Fourth battalion of S-400 systems assumes combat duty in Crimea near border with Ukraine

DZHANKOI /Republic of Crimea/, November 29. /TASS/. The fourth battalion of S-400 air defense missile systems has assumed combat duty in Crimea near the Russian-Ukrainian border, the Black Sea Fleet’s press office reported on Thursday.
"Today, the combat teams of S-400 Triumf surface-to-air missile systems from a large air defense unit of the Southern Military District’s Air Force and Air Defense Army have assumed combat duty to provide for Crimea’s air defense," the press office said in a statement.
The S-400 crews moved to their positions, deployed launchers, determined their location and guidance on the ground and started detecting and tracking targets in their combat mission on Thursday for the Crimean Peninsula’s air defense.
As was reported earlier, the third S-400 battalion assumed combat duty in Crimea’s Yevpatoria in September to protect the Russian airspace. The similar air defense missile systems went on combat duty in Feodosiya in January 2017 and in Sevastopol in January 2018 to protect the Russian airspace in Crimea.
The S-400 Triumf mobile multi-channel air defense missile system is designed to defend vital military facilities and infrastructural installations and features better capabilities compared to its S-300PM predecessor.
Russia’s S-400 Triumf is the latest medium-and long-range surface-to-air missile system that went into service in 2007. It is designed to destroy aircraft, cruise and ballistic missiles, and can also be used against ground installations. The S-400 can engage targets at a distance of 400 km and at an altitude of up to 30 km.
Russia to Build New Missile Early-Warning Radar Station in Crimea

Russia plans to build a new missile early-warning radar station in Crimea next year, the Interfax news agency reported on Thursday, citing a Crimean security source.
News that a new military facility will be built in Crimea, which Russia annexed from Ukraine in 2014, follows Russia's seizure of three Ukrainian navy vessels off the coast of the peninsula on Sunday.
The new radar station — which will be able to track ballistic and cruise missiles from a long distance — will be built near the port of Sevastopol where Russia's Black Sea fleet is based, the source told the news agency.
Interfax reported earlier on Thursday that Russia was also working on a new technical system to allow it to better track shipping around the peninsula in order to protest its maritime borders.
The Russian Ministry of Defense said on Wednesday it would deploy a new battalion of S-400 surface-to-air missile systems on the Crimean peninsula by the end of the year.
Australian police offer reward for information about murder of ex-KGB colonel.

Police in the Australian state of Queensland have offered a $250,000 (US $182,000) reward for information that can help solve the murder of a former Soviet KGB colonel 18 years ago. The victim, Gennadi Bernovski, worked in the domestic wing of the Soviet KGB, until his retirement, which coincided with the dissolution of the USSR. In 1996, he moved to Australia with his family and bought a house in Benowa Waters, a luxury suburb of Gold Coast, a city located south of Brisbane on the country’s east coast. But on the evening of July 24, 2000, Bernovski was shot to death outside his home by what witnesses said were two men in combat diver suits. They reportedly opened fire on Bernovski with a semi-automatic weapon, wounding him fatally in the stomach. He was dead within a few minutes. It is believed that the assailants sailed to Bernovski’s waterfront property on an inflatable boat, or swam there, having first sailed to the nearby seaside.
Since Bernovski’s murder, Australian authorities have refused to answer questions about how the former KGB colonel came to settle in the country, and whether he was given political asylum by the Australian government. They have also refused to answer questions relating to Bernovski’s citizenship at the time of his murder. Some reports have pointed out that he was an Australian citizen when he was murdered. Furthermore, little is known about his financial status or sources of income, though it is believed that he had access to “multiple bank accounts in Russia and Australia”. On Thursday, spokespersons for the Australian Federal Police and the Queensland Police Department refused to provide information on the investigators’ current working hypothesis about who might have been responsible for Bernovski’s murder. They were also asked whether some family members of the late former KGB officer continue to reside in Australia under assumed names, but declined to comment.
A spokeswoman for the Federal Department of the Australian Attorney-General said that the new reward offer was aimed at “cracking a cold case”, which is a routine police practice for unsolved crimes. She did not comment, however, on media speculation that police sought to interview another Russian national, Oleg Kouzmine, who was living in Gold Coast during the time of Bernovski’s murder. According to reports, Kouzmine is now living in another country, which means that Australian authorities would need to seek the cooperation of a foreign law enforcement agency in order to gain access to him. However, the Attorney-General Department spokeswoman told reporters on Thursday that, “as a matter of longstanding practice, the Australian government does not confirm whether it has made a request for assistance to a foreign country in a criminal matter”.
► Author: Ian Allen
Monday, November 5, 2018
CIA suffered ‘catastrophic’ compromise of its spy communication system

The United States Central Intelligence Agency suffered a “catastrophic” compromise of the system it uses to communicate with spies, which caused the death of “dozens of people around the world” according to sources. This is alleged in a major report published on Friday by Yahoo News, which cites “conversations with eleven former US intelligence and government officials directly familiar with the matter”. The report by the online news service describes the compromise of an Internet-based covert platform used by the CIA to facilitate the clandestine communication between CIA officers and their sources —known as agents or spies— around the world.
According to Yahoo News, the online communication system had been developed in the years after 9/11 by the US Intelligence Community for use in warzones in the Middle East and Central Asia. It was eventually adopted for extensive use by the CIA, which saw it as a practical method for exchanging sensitive information between CIA case officers and their assets in so-called ‘denied areas’. The term refers to regions of the world where face-to-face communication between CIA case officers and their assets is difficult and dangerous due to the presence of non-state adversaries like the Taliban, al-Qaeda or the Islamic State. However, it appears that the system was flawed: it was too elementary to withstand sustained scrutiny by Internet-savvy counterintelligence experts working for state actors like Iran, China or Russia.
In September of 2009, Washington made a series of impressively detailed revelations about the advanced status of Iran’s nuclear program. These angered Tehran, which redoubled its efforts to stop the US and others from acquiring intelligence information about the status of its nuclear program. Some sources told Yahoo News that one of the CIA assets inside Iran’s nuclear program was convinced by the Iranians to become a double spy. He proceeded to give Tehran crucial information about the CIA’s online communication system. Based on these initial clues, the Iranians allegedly used Google-based techniques “that one official described as rudimentary” to identify an entire network of CIA-maintained websites that were used to communicate with assets in Iran and elsewhere. The Iranians then kept tabs on these websites and located their users in order to gradually unravel an entire network of CIA agents inside their country. Around that time, Iranian media announced that the Islamic Republic’s counterintelligence agencies had broken up an extensive CIA spy ring consisting of more than 30 informants.
The Yahoo News report says that the CIA was able to successfully exfiltrate some of its assets from Iran before the authorities were able to apprehend them. The agency also had to recall a number of undercover officers, after they were identified by the Iranians. The effects of the compromise, however, persisted on a global scale, according to former US intelligence officials. In 2011 and 2012, another network of CIA spies was busted in China, leading to the arrest and execution of as many as three dozen assets working for the US. Many, says Yahoo News, believe that the Iranians coached the Chinese on how to use the CIA’s online communication system to identify clandestine methods and sources used by the agency.
Along with other specialist websites, IntelNews has monitored these developments as they took place separately in Iran and China. However, the Yahoo News report is the first to piece together these seemingly disparate developments and suggest that they were likely triggered by the same root cause. What is more, the report suggests that the CIA had been warned about the potential shortcomings of its online communication system before 2009, when the first penetrations began to occur. In response to the compromise, the CIA has reportedly modified, and at times completely abandoned, its online communication system. However, the implications of the system’s compromise continue to “unwind worldwide” and the CIA is “still dealing with the fallout”, according to sources. The effects on the agency’s operational work are likely to persist for years, says Yahoo News.
► Author: Joseph Fitsanakis
Suicide bomber who attacked Russian spy agency identified as ‘anarchist-communist’

A teenager who killed himself with an improvised explosive device in the lobby of a regional office of Russia’s domestic intelligence agency appears to have identified himself as an “anarchist-communist” on social media. At 8:52 am local time on Wednesday, the 17-year-old entered the regional office of Russia’s Federal Security Service (FSB) in the city of Archangelsk, located 800 miles north of Moscow. On CCTV footage released by the Russian security services, he is seen reaching into his backpack and taking out an object, which soon exploded, killing him and wounding three others.
The bomber was later identified in the Russian media as Mikhail Zhlobitsky, a student at a local technical college. Within hours, reports pointed to posts made on social media platforms by Zhlobitsky, who used several online aliases, including that of “Sergey Nechayev”, one of Russia’s leading 19th-century anarchists, who died in prison for advocating terrorism as a means of revolution. Shortly before the attack, someone using the alias “Valeryan Panov” commented on the social messaging application Telegram that he was about to bomb the FSB in Archangelsk. In the comment, which was posted on an anarchist forum, the user said that he had decided to act “because the FSB falsifies cases and tortures people”. The user added that he would probably die in the attack because he had to manually detonate the improvised explosive device he was carrying with him. He concluded his message with the words: “I wish you a glorious future of anarchist communism!”.
The activities of militant Russian anarchists and anarcho-communists date back to the mid-19thcentury; anarchist militants are responsible for numerous assassinations of senior Russian officials, including Emperor Alexander II, who was killed by a Russian anarchist in 1881. But the movement was ruthlessly suppressed by the Soviet state and today the FSB and other Russian security services are actively monitoring the remnants of the Russian anarchist movement. These include the Confederation of Revolutionary Anarcho-Syndicalists, the group Autonomous Action, and the Siberian Confederation of Labor. Large sections of these groups have now moved underground, as the government of Russian President Vladimir Putin has named anarchists as primary enemies of order and security in the Russian Federation. Earlier this month, another Russian teenager, Vladislav Roslyakov, killed himself after shooting 19 students and teachers at a technical college in Kerch, a Black Sea port city in Russian-annexed Crimea. No political motive for the attack has been reported.
► Author: Joseph Fitsanakis
Denmark recalls its envoy from Tehran, accuses Iran of assassination plot
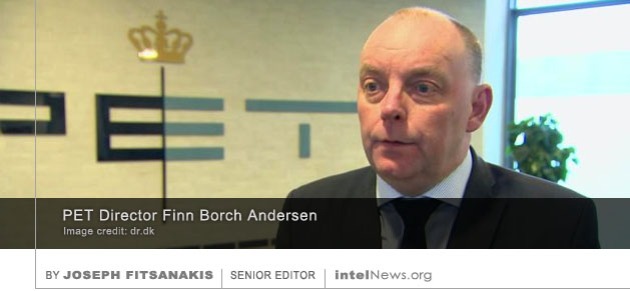
The Danish government has recalled its ambassador from Iran and has accused the intelligence services of the Islamic Republic of plotting an assassination operation on Danish soil. Danish government officials also said that Copenhagen would seek to impose further economic and diplomatic sanctions on Tehran, in coordination with the European Union. The accusations against Iran were leveled during an emergency news conference in the Danish capital on Tuesday, led by Anders Samuelsen, Denmark’s Minister of Foreign Affairs, and Finn Borch Andersen (pictured), Director of the Danish Security and Intelligence Service, known as PET.
The two men said that “an Iranian intelligence agency” had planned “an attack on Danish soil”, which Defense Minister Samuelsen condemned as “completely unacceptable”. PET Director Andersen said that a Norwegian national of Iranian background had been arrested in Sweden on October 21, and was now in custody awaiting extradition to Denmark. The arrestee is an employee of Iranian intelligence, said Andersen, and had been observed conducting surveillance against a Danish-based leading member of an Iranian separatist group. The alleged target is a member of the Arab Struggle Movement for the Liberation of Ahvaz (ASMLA), a hardline separatist group campaigning for a separate homeland for Iran’s Arab minority. Approximately 2 percent of Iranians (around 1.5 million people) belong to the country’s ethnic Arab population. Most of them are concentrated in Khuzestan, a region in Iran’s oil-rich southwest, which borders neighboring Iraq. Some of these ethnic Arabs seek autonomy from Tehran, which they see as an alien regime. ASMLA represents the militant wing of Iran’s separatist Arab community and has a history of staging terrorist attacks inside Iran. Last September, the group claimed it was behind an armed attack on a military parade in the city of Ahvaz —a major urban center in Iran’s Arab-speaking region— which killed 24 people, including some women and children. Later, however, a representative of the group retracted the claim.
On Tuesday, several Iranian officials issued strong denials of the Danish government’s allegations. Speaking in Tehran, Iranian Foreign Ministry Spokesman Bahram Qassemi dismissed Denmark’s claims as “spiteful”. He added that the timing of reports linking Iran to assassination operations on European soil were suspect and described them as “a plot by [Iran’s] enemies to damage Tehran’s growing relations with European countries”. Earlier this month, France seized the financial assets of individuals whom it described as Iranian spies, after blaming Tehran for a foiled bomb attack in Paris. The move followed the arrest of six people in France, Germany and Belgium, who allegedly planned to bomb the annual conference of the National Council of Resistance of Iran (NCRI) last June. The NCRI is led by Mujahedin-e Khalq (MEK), a militant group with roots in radical Islam and Marxism, which Iran sees as a terrorist organization.
► Author: Joseph Fitsanakis
Tuesday, October 9, 2018
France freezes assets of Iranian spies in response to foiled terror attack in Paris

France has seized the financial assets of two Iranian spies and frozen all assets belonging to the Iranian Ministry of Intelligence, in response to a foiled bomb attack in Paris, which the French government has blamed on Tehran. The alleged bomb attack was uncovered on June 30 of this year, when members of Belgium’s Special Forces Group arrested a married Belgian couple of Iranian descent in Brussels. The couple were found to be carrying explosives and a detonator. On the following day, German police arrested an Iranian diplomat stationed in Iran’s embassy in Vienna, Austria, while another Iranian man was arrested by authorities in France, reportedly in connection with the three other arrests.
All four individuals were charged with a foiled plot to bomb the annual conference of the National Council of Resistance of Iran (NCRI) that took place on June 30 in Paris. The NCRI is led by Mujahedin-e Khalq (MEK), a militant group with roots in radical Islam and Marxism. The MEK was designated as a terrorist group by the European Union and the United States until 2009 and 2012 respectively. But it has since been reinstated in both Brussels and Washington, reportedly because it provides the West with a vehicle to subvert the Iranian government. France, Germany and Belgium allege that the aborted bombing plot was an attempt by Iran to disrupt the close relations between the MEK and Western governments.
On Tuesday, Paris announced the seizure of assets of two of the men who were arrested in June and July. One is an accredited Iranian diplomat identified as Assadollah Asadi, who is believed to be an official-cover intelligence officer. The other man is Saeid Hashemi Moghadam, who was arrested by French authorities. He is believed to be an Iranian sleeper agent. All assets belonging to the Islamic Republic’s Ministry of Intelligence were also been frozen, effective immediately, it was announced. In a joint statement, the French ministers of foreign affairs, economics and the interior said that the move reflected the France’s “commitment to fight terrorism, in all its manifestations […], especially on its territory”. The statement added that “the extremely heinous act envisaged on our territory could not go without a response”.
The Iranian government has denied all connection to the alleged plot in Paris and has dismissed the incident a “false flag” operation staged by MEK in cooperation with Tehran’s “enemies at home and abroad”.
► Author: Joseph Fitsanakis
Britain sees Russian government hackers behind Islamic State cyber group

A new report by the British government alleges that the so-called ‘Cyber Caliphate’, the online hacker wing of the Islamic State, is one of several supposedly non-state groups that are in fact operated by the Russian state. The group calling itself Cyber Caliphate first appeared in early 2014, purporting to operate as the online wing of the Islamic State of Iraq and Syria (ISIS), which was later renamed Islamic State. Today the Cyber Caliphate boasts a virtual army of hackers from dozens of countries, who are ostensibly operating as the online arm of the Islamic State. Their known activities include a strong and often concentrated social media presence, as well as computer hacking, primarily in the form of cyber espionage and cyber sabotage.
But an increasing number of reports, primarily by Western government agencies, have claimed in recent years that the Cyber Caliphate is in fact part of a Russian state-sponsored operation, ingeniously conceived to permit Moscow to hack Western targets without retaliation. On Wednesday, a new report by Britain’s National Cyber Security Centre (NCSC) described the Cyber Caliphate and other similar hacker groups as “flags of convenience” for the Kremlin. The report was authored by the NCSC in association with several British and European intelligence agencies. American spy agencies, including the National Security Agency and the Federal Bureau of Investigation, also helped compile the report, according to the NCSC. The report names several hacker groups that have been implicated in high-profile attacks in recent years, including Sofacy, Pawnstorm, Sednit, Cyber Berkut, Voodoo Bear, BlackEnergy Actors, Strontium, Tsar Team, and Sandworm. Each of these, claims the NCSC report, is “an alias of the Main Directorate of the General Staff of Russia’s Armed Forces”, more commonly known as the GRU. The report concludes that Cyber Caliphate is the same hacker group as APT 28, Fancy Bear, and Pawn Storm, three cyber espionage outfits that are believed to be online arms of the GRU.
The NCSC report echoes the conclusion of a German government report that was leaked to the media in June of 2016, which argued that the Cyber Caliphate was a fictitious front group created by Russia. In 2015, a security report by the US State Department concluded that despite the Cyber Caliphate’s proclamations of connections to the Islamic State, there were “no indications —technical or otherwise— that the groups are tied”. In a statement issued alongside the NCSC report on Wednesday, Britain’s Secretary of State for Foreign and Commonwealth Affairs, Jeremy Hunt, described the GRU as Moscow’s “chosen clandestine weapon in pursuing its geopolitical goals”. The Russian government has denied these allegations.
► Author: Ian Allen |
Missing Saudi journalist 'murdered and dismembered' inside his country's consulate in Istanbul while fiancée waited outside, claims friend

Turkish officials have claimed a missing Saudi journalist was killed inside his own country's consulate in Istanbul last week.
Jamal Khashoggi was said to have been killed in what Turkish police claimed was the deliberate targeting of a prominent critic of the Gulf kingdom's rulers.
Mr Khashoggi entered the Saudi consulate in Istanbul to get documents for his forthcoming marriage, according to reports.
Saudi officials say he left shortly afterwards but his fiancee, who was waiting outside, said he never came out.
A friend of a Mr Khasoggi today said officials told him to "make your funeral preparations".

Turan Kislakci, a friend of Jamal Khashoggi and the head of the Turkish-Arab Media Association, said officials also told him they "have evidence he was killed in a barbaric way" and dismembered.
Saudi officials have denied the allegations that Mr Khashoggi was killed as "baseless".
One Turkish official said authorities believe Mr Khashoggi was killed at the Saudi consulate, while another said it was a "high possibility".

Turkish police said: "The initial assessment of the Turkish police is that Mr Khashoggi has been killed at the consulate of Saudi Arabiain Istanbul.
"We believe that the murder was premeditated and the body was subsequently moved out of the consulate."
The President of Turkey said the Saudi Consulate and Istanbul's airports are being closely monitored for clues.
Recep Tayyip Erdogan said today that he is still hopeful that Jamal Khashoggi is alive.
"God willing we will not be faced with the situation we do not desire," he added.
The comment apparently referred to Turkish officials saying they believed that Mr Khashoggi was killed at the Saudi Consulate after disappearing on Tuesday.
Mr Erdogan called Mr Khashoggi a "journalist and a friend".
He said he was personally following the case and would announce the results of the investigation at an undisclosed time.
Mr Khashoggi, a former newspaper editor in Saudi Arabia and adviser to its former head of intelligence, left the country last year saying he feared retribution for his growing criticism of Saudi policy in the Yemen war and its crackdown on dissent.
Subscribe to:
Posts (Atom)



